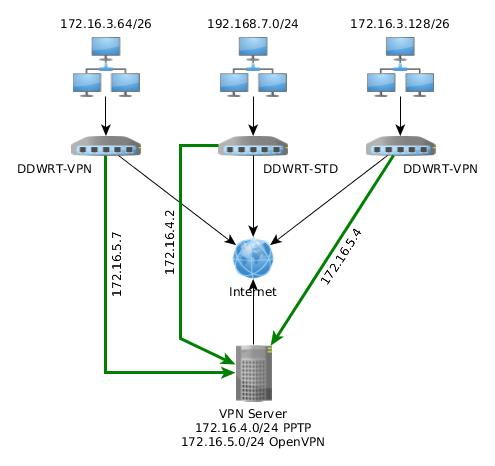
 Say you have the following topology:
Say you have the following topology:
- Ubuntu VPN server
- 2x DDWRT routers with VPN firmware and openvpn support
- 1x DDWRT router that only supports PPTP
What we wanted to do is for each LAN to be able to communicate with the other two LANs.
Let's start by setting up OpenVPN on Ubuntu by following this guide at Ubuntu web site
Change the topology to subnet , then you need to inform VPN Server about the routes for the two LAN networks that will be connecting via OpenVPN.
This will add routes in the Server's routing table
route 172.16.3.128 255.255.255.192 172.16.5.1 route 172.16.3.64 255.255.255.192 172.16.5.1
Note that each route has OpenVPN's ip address at the end. This is a workaround of a known bug when using subnet topology.
Now let's inform each router about routes to the rest of the LANs connected to our VPN.
push "route 172.16.3.64 255.255.255.192" push "route 172.16.3.128 255.255.255.192" push "route 192.168.7.0 255.255.255.0"
This will make each connecting router to add these routes to it's routing table. Now there is a small problem, let's say LAN 172.16.4.64/24 connects to the VPN server and receives this list of routes, the router will already have a route for 172.16.4.64/24 and the it will get a new one having VPN Server's PPP address as gateway. As a result the router will try to route packets destined for it's own LAN to the VPN Server.
To avoid that you need to create a per-client configuration file. This is enabled using client-config-dir ccd where ccd is a directory that will hold per client configuration files.
Clients are identified by their certificate common name and this is the filename of each configuration file.
So for common name LAN1 crate a file LAN1 inside ccd directory with contents:
ifconfig-push 172.16.5.4 255.255.255.0 iroute 172.16.3.128 255.255.255.192
this will assign a specific IP address to LAN1 client and it will omit 172.16.4.64/24 route from pushed routes.
Following the same logic, create a file for LAN2 inside ccd directory:
ifconfig-push 172.16.5.7 255.255.255.0 iroute 172.16.3.64 255.255.255.192
Complete OpenVPN configuration file:
port 1194 proto udp dev tun ca ca.crt cert server.crt key server.key # This file should be kept secret dh dh1024.pem server 172.16.5.0 255.255.255.0 ifconfig-pool-persist ipp.txt topology subnet push "route 172.16.3.64 255.255.255.192" push "route 172.16.3.128 255.255.255.192" push "route 192.168.7.0 255.255.255.0" client-config-dir ccd route 172.16.3.128 255.255.255.192 172.16.5.1 route 172.16.3.64 255.255.255.192 172.16.5.1 client-to-client keepalive 10 120 max-clients 10 persist-key persist-tun status openvpn-status.log log openvpn.log verb 3
DEFAULT_FORWARD_POLICY="ACCEPT"
Finally let's enable IPv4 routing, edit /etc/sysctl.conf and set net.ipv4.ip_forward=1
DD-WRT Router setup
Setup OpenVPN for LAN1 & LAN2 as per http://www.dd-wrt.com/wiki/index.php/OpenVPN#OpenVPN_in_DD-WRT
Remember to use the same settings for protocol and compression as in server configuration.
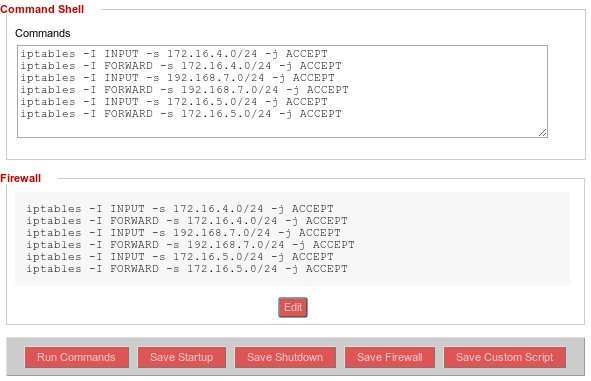
Next you need to setup iptables rules if you have firewall enabled. The following rules will allow traffic from OpenVPN and PPTP clients as well as LAN3.
Go to Administration -> Commands and paste these rules in command shell:
iptables -I INPUT -s 172.16.5.0/24 -j ACCEPT iptables -I FORWARD -s 172.16.5.0/24 -j ACCEPT iptables -I INPUT -s 172.16.4.0/24 -j ACCEPT iptables -I FORWARD -s 172.16.4.0/24 -j ACCEPT iptables -I INPUT -s 192.168.7.0/24 -j ACCEPT iptables -I FORWARD -s 192.168.7.0/24 -j ACCEPT
and click Save Firewall button.
This will allow traffic from VPN subnets ans LAN3 subnet to pass through the router.
LAN3 VPN using PPTP
Setup VPN Client
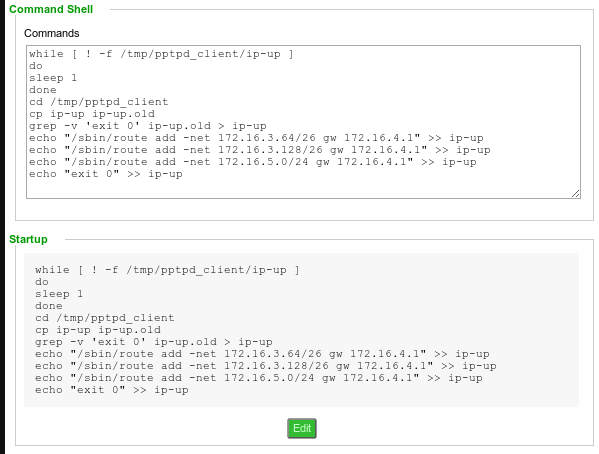
Getting routes to be added after VPN connection is established is a bit tricky at least for TL-WR740N router running DDWRT.
In order to add routes after PPTP connection is established you need to modify ip-up script in /tmp/pptpd_client. The problem is that this script is generated when pptpd starts.
To modify it you need to add a startup script that will wait for this file to be created and then append whatever custom routes are needed.
Saving this as startup script will do the trick:
while [ ! -f /tmp/pptpd_client/ip-up ] do sleep 1 done cd /tmp/pptpd_client cp ip-up ip-up.old grep -v 'exit 0' ip-up.old > ip-up echo "/sbin/route add -net 172.16.3.64/26 gw 172.16.4.1" >> ip-up echo "/sbin/route add -net 172.16.3.128/26 gw 172.16.4.1" >> ip-up echo "/sbin/route add -net 172.16.5.0/24 gw 172.16.4.1" >> ip-up echo "exit 0" >> ip-up
Done
Now you should be able to ping hosts from one LAN to another.
If something is not working try to ping each router from VPN Server and work your way to each LAN. This can help pinpoint at which hop the problem lies.
Check routing tables on VPN Server and each router using ip route
